Benefits of free online time clock
Online time clock software is a category of computer software that allows its users to record time spent on tasks. Online time clock software...
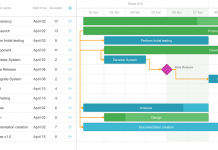
Advantages of Office Timeline
Office timeline is one of the highly interactive timeline creator which are the best choice for using as project scheduler. This is the right...
Why Having Many Instagram Views Is Beneficial
Instagram has become one of the world's most popular social media apps, with over a billion users. However, there is no denying that some...
Looking For Voip International Call Rates?
We are in the era of mobile phones right now. The phone system is still crucial for businesses, though. Every Singaporean company is required...
What are the benefits of hiring consulting services?
Nowadays, people have many ways to earn money. They used to work in various types of organizations. If they decide to start a new...
Get Ultimate high-Speed Backup Recovery Solution for your Business
In recent years, technology is growing so fast, and it is used everywhere like business, education, etc. Technology helps to grow your country in...
Things That Might Interfere with Your Wi-Fi
One of the benefits of using Wi-Fi to copy documents is that you do not have to string a cable from your computer to...
How to choose the best and cheap printer?
Having fun in the vacation holidays with the family members is great always and this could help everyone to relieve our stress from the...
The designs can be created effectively with the computer programs
You can learn the graphics design by checking out the tutorials available in the online. All the basics about the graphics design are completed...
In-Depth Information About The Crest Penetration Testing Procedure
Ethical hacking, often known as crest penetration testing methodology, evaluates a company's security protocols by carrying out simulated attacks similar to those a real...